Karma for Slack: security documentation
Updated: May 11 2020
Security at Karma
Introduction
Karma's mission is to build stronger, happier teams. Set goals, track performance and reward excellence. We believe that we need to make your data secure and that protecting it is one of our most important responsibilities. We're committed to being transparent about our security practices and helping you understand our approach.
Protecting Customer Data
The focus of Karma bot security program is to prevent unauthorized access to customer data.
Secure By Design
Karma's product security team has built a robust secure development lifecycle, which primarily leverages GitLab CI/CD. All identified vulnerabilities are validated for accuracy, triaged, and tracked to resolution.
Encryption
Data in transit
All data transmitted between Karma clients and the Karma service is done so using strong encryption protocols. Karma supports the latest recommended secure cypher suites to encrypt all traffic in transit, including the use of TLS 1.3 protocols, AES256 encryption, and SHA2 signatures. We utilize CloudFlare to enhance encryption and security.
Data at rest
Data at rest in Karma's production network uses the Advanced Encryption Standard (AES) algorithm to encrypt data at rest. AES is widely used because both AES256 and AES128 are recommended by the National Institute of Standards and Technology (NIST) for long-term storage use (as of November 2015), and AES is often included as part of customer compliance requirements.
Encryption at the storage device layer
In addition to the storage system level encryption described above, in most cases data is also encrypted at the storage device level, with at least AES128 for hard disks (HDD) and AES256 for new solid state drives (SSD), using a separate device-level key (which is different than the key used to encrypt the data at the storage level). As older devices are replaced, solely AES256 will be used for device-level encryption.
Authentification
Karma is using Slack as authentification provider. We do not keep any passwords or tokens on our servers. Slack is well known for robust security protocols. If a user is removed from Slack or disabled in Slack, they won't be able to log into a Karma dashboard and all the user data will be removed from Karma server.
Access Control
Provisioning
To minimize the risk of data exposure, Karma adheres to the principles of least privilege and role-based permissions when provisioning access---workers are only authorized to access data that they reasonably must handle in order to fulfil their current job responsibilities. All production access is reviewed at least quarterly.
Authentication
To further reduce the risk of unauthorized access to data, Karma employs multi-factor authentication for all access to systems with highly classified data, including our production environment, which houses our customer data.
Password Management
Karma requires personnel to use an approved password manager. Password managers generate, store, and enter unique and complex passwords to avoid password reuse, phishing, and other password-related risks.
Data retention and disposal
Customer data is removed immediately upon deletion by the end user. Karma hard deletes all information from currently running production systems (including team, channel names and karma descriptions) and backups are destroyed within 14 days.
Karma's hosting providers are responsible for ensuring removal of data from disks is performed in a responsible manner before they are repurposed
Responding to Security Incidents
Karma has established policies and procedures (also known as runbooks) for responding to potential security incidents. All security incidents are managed by Karma Team. The runbooks define the types of events that must be managed via the incident response process and classifies them based on severity. In the event of an incident, affected customers will be informed via email from our customer experience team.
External Validation
Security Compliance Audits
Karma is continuously monitoring, auditing, and improving the design and operating effectiveness of our security controls. These activities are regularly performed by the Karma team.
Conclusion
We have an existential interest in protecting your data. Every person, team, and organization deserves and expects their data to be secure and confidential. Safeguarding this data is a critical responsibility we have to our customers, and we continue to work hard to maintain that trust. Please contact our team if you have any questions or concerns.
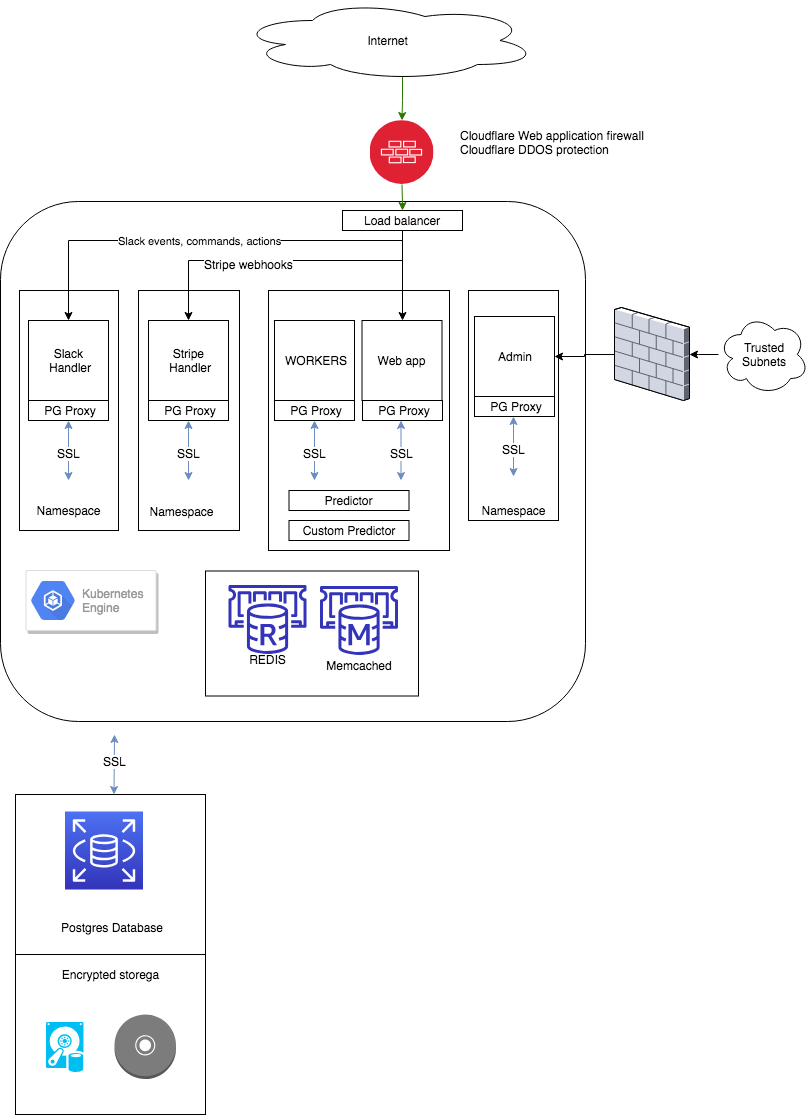
Overall Karmabot for Slack app architecture.
Updated 8 months ago